Content
Check Your Ports – test udp port
Open Slot Examine Device:
A port is a number that represents an entry to a company that levels to the network.
In computer system networks, an available slot is a port that presently makes use of (open) by a service. An available slot can be made use of to deliver or/and get data over the network.
- To check separately, choose 'individual', input a legitimate port number, and also choose 'Scan'.
- So make use of the Open port mosaic as well as if your port is closed, connect with your ISP and also see if they will allow you to utilize it.
- You can additionally utilize the Neighbor Map and also Course Audience devices in ETS for a noticeable summary of how your network is transmitting.
- Discover product guides, documents, training, onboarding info, and assistance posts.
- With the SNMP MIB web browser, you can query SNMP-managed tools to check out configurations and also various other MIB characteristics.
- Network ports are the communication endpoints for an equipment that is linked to the Internet.
- Ports differ in their procedures as well as the types of solutions they provide.
TCP slots and UDP slots. Open port inspection resource can easily inspect the condition of a TCP slot.
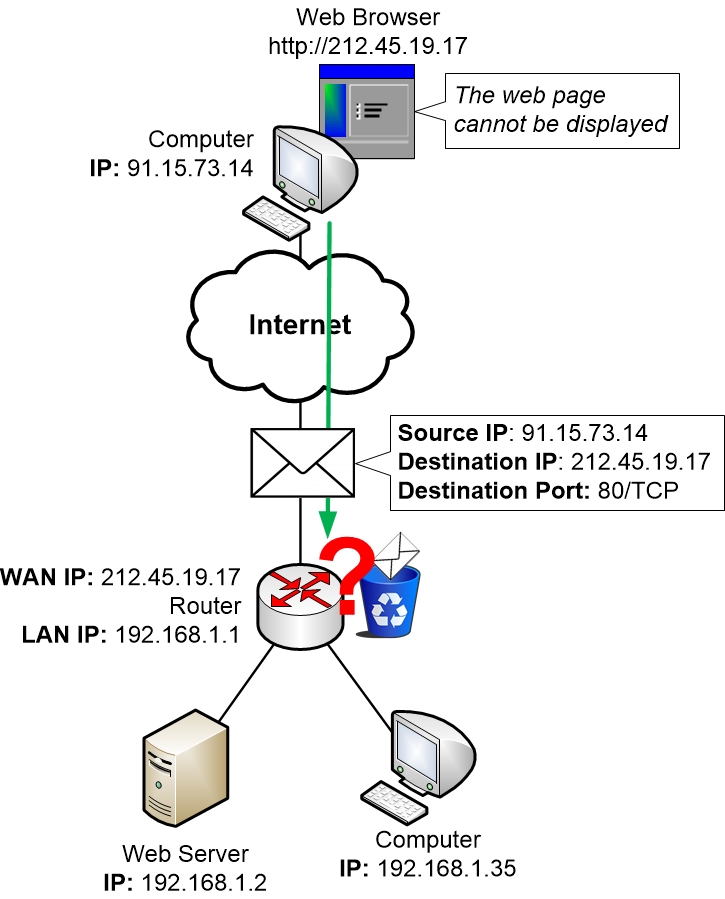
An example may be your internet browser on the client-side and also a web server as the remote control server.
The internet server makes use of the default slot 80 for HTTP or slot 443 for HTTPS to pay attention and hang around for relationships. An available port inspection device may be made use of to inspect if the slot is presently open or even not on an intended device.
It is actually like a port examination, using this device you can likewise spot slot forwarding condition.
You can likewise use an available port examination resource to remotely check out if your web server is actually being blocked out by a firewall program.
Slot Scanner: A slot scanner is actually a resource that may be used to browse a stable of slots.
An advanced or port mosaic may check some handle or perhaps a complete system looking for slots that are available. In computer safety and also hacking it is extensively used to look for difficult open slots that suppose to become near or screen. An available port feels like an open door or a home window. With the ideal know-how, it is achievable to use this port to become part of the distant personal computer.
Utilizing and also running a routine port check is actually a good strategy to discover open slots and shut all of them. , if an available port is located it is actually also used to recognize why and who open it.
.
What Is A Port Scanner? – port checker
There are actually some incredibly helpful devices that could be utilized to browse the system address for open slots. Making use of such tools can easily also find address inside the association that needs to have to be eliminated.
An instance of network ports scanner device is actually Nmap. Utilizing it you can scan complete subnet. It assists numerous browse techniques like TCP SYN check as well as TCP ACK scan. Advanced use of the device may spot what is the solution (method) that open the port as well as the operating system backing this solution.
On-line slot scanning device:
The outdated art of port scanning is actually still operating. Also thou that today there is actually a much more safe approach to shut and monitor ports and solutions in the workplace.
. An Intrusion detection unit (IDS) could be used to keep track of the system.
With the accelerated of brand-new tools, an on-line port scanner resource can easily be used as a source to scan an environment. Browsing from outside the company.
An online slot scanning device is actually a slot scanning device like any other port scanner. The only deferent is that it operates coming from outside your network. re: a website-- online.
If you have needless open ports on your computer/device that requires to be shut, it is a terrific device that may be actually made use of to check out.
Companies that depend on the Internet (like web browsers, web pages, and file transfer services) rely upon specific ports to transmit and receive information. Developers use file transfer protocols (FTPs) or SSH to operate encrypted tunnels all over pcs to share relevant information in between bunches.
The moment a company is actually operating on a specific slot, you can't operate other services on it. For example, beginning Apache after you've actually started Nginx on slot 80 will result in a stopped working procedure since the port is already in operation.

Open ports become risky when valid companies are port checker actually manipulated with safety and security susceptabilities or malicious companies are actually launched to an unit through malware or social planning, cybercriminals may make use of these solutions along with open slots to obtain unwarranted accessibility to delicate data.
Closing unused slots lowers your protection danger by minimizing the amount of strike angles your company is exposed to.